Security Management
ISO/IEC 2700x - Standards Series of Corporate Security
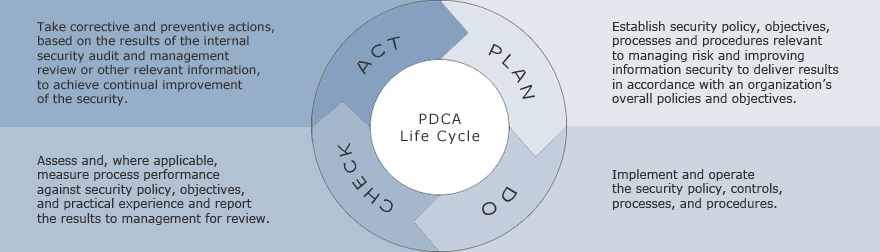
The standard is one of the most comprehensive examples of how to apply PDCA to the improvement of security, including sustaining a desired security state or posture for an operational system. It describes how to establish, implement, operate, monitor, review, maintain, and improve an organization's security management system.
Management Commitment to Security
Organizational leaders, including board directors, business executives, chief information officers, and managers of corporate audit, security, legal, line-of-business, privacy, and supply chain, all must play a role in making and reinforcing the business case for effective security. Trust, reputation, brand, stakeholder value, and customer retention are at stake if security management is performed poorly. Attentive organizations are much more competent in using security to mitigate risk if their leaders treat it as essential to the business and are aware and knowledgeable about security issues.
It is difficult, if not impossible, to sustain security improvement and move it into everyday organizational culture and practice without senior management commitment and ongoing reinforcement.
Application
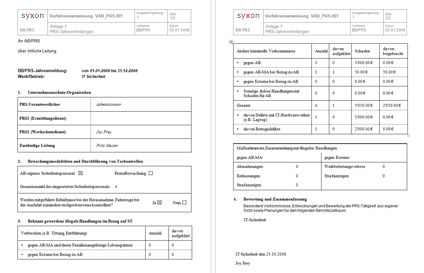
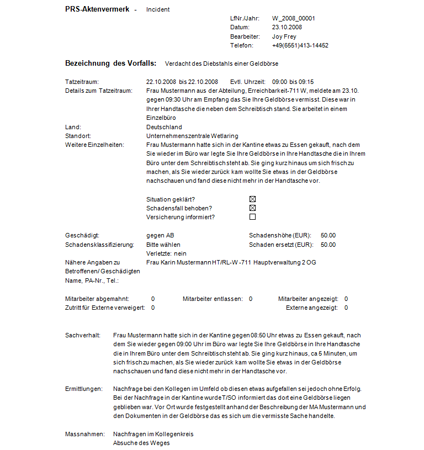
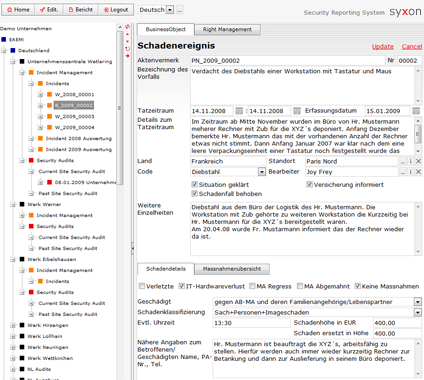
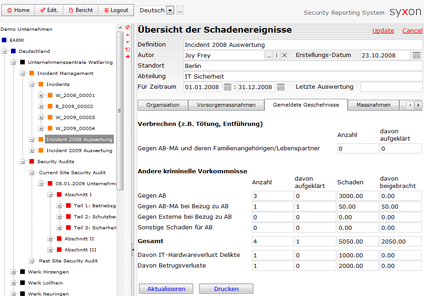
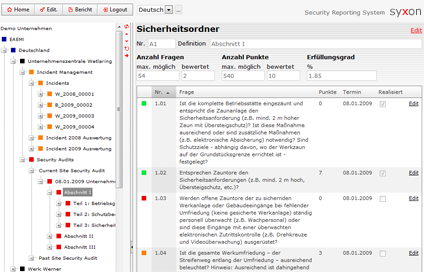
All our solutions are highly client specific, therefore we only show small fragments of selected modules of the application.
The reports are generated out of the system by just pressing a button. The document templates are specified by the customer, usually in MS Word, Excel or PDF-format. Besides the export also an import of data from other applications is available.
The modules used here are:
- Security Management
- Incident Management
- Security Audits
- Measure Management
- Reporting Management
Screenshots